CTFshow-web21-28
web21
- 题目:
- burp抓包利用Intruder模块进行爆破,在根据hint1里的提示知道这是一个tomcat认证爆破,所以标记Authorization: Basic
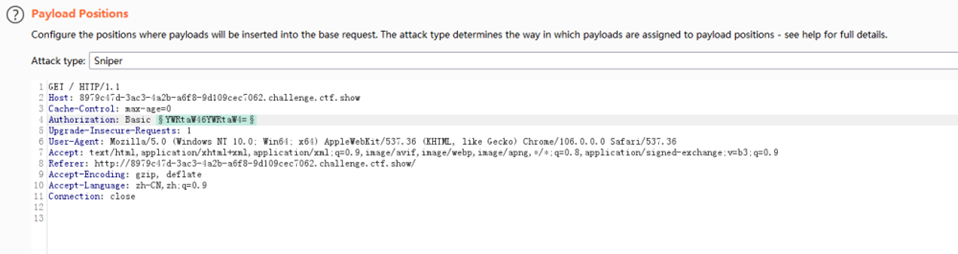
- Authorization字段后面的值经过了base64的加密,所以爆破时也要进行相应的加密
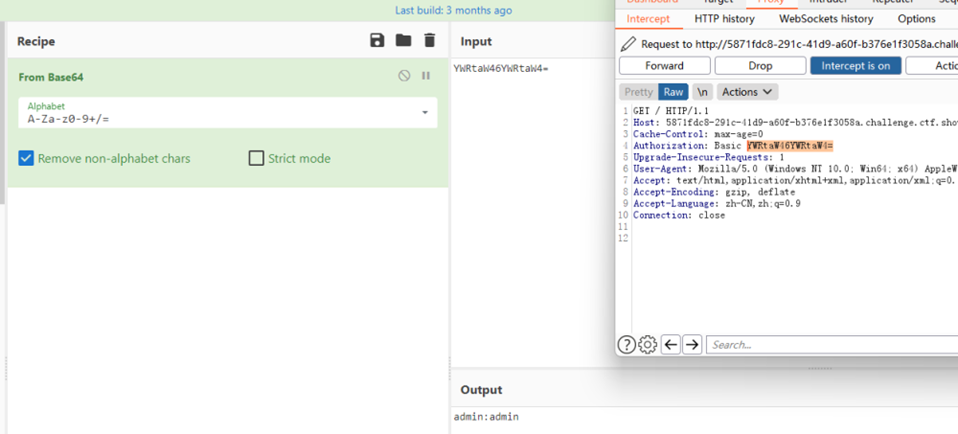
- Payload sets的设置,字典利用题目给的附件,用户名猜一手admin,最后也是证明猜对了

web22
- 域名失效了做不了

web23
- 题目:
- 源码:
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-03 11:43:51
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-03 11:56:11
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
include('flag.php');
if(isset($_GET['token'])){
$token = md5($_GET['token']);
if(substr($token, 1,1)===substr($token, 14,1) && substr($token, 14,1) ===substr($token, 17,1)){
if((intval(substr($token, 1,1))+intval(substr($token, 14,1))+substr($token, 17,1))/substr($token, 1,1)===intval(substr($token, 31,1))){
echo $flag;
}
}
}else{
highlight_file(__FILE__);
}
?>
- 分析源码编写php脚本:
<?php
for ($i=0;$i<10000;$i++) {
$token = md5($i);
if (substr($token, 1, 1) === substr($token, 14, 1) && substr($token, 14, 1) === substr($token, 17, 1)) {
if ((intval(substr($token, 1, 1)) + intval(substr($token, 14, 1)) + substr($token, 17, 1)) / substr($token, 1, 1) === intval(substr($token, 31, 1))){
echo 'token'.$i.'md5'.$token;
}
}
}
?>
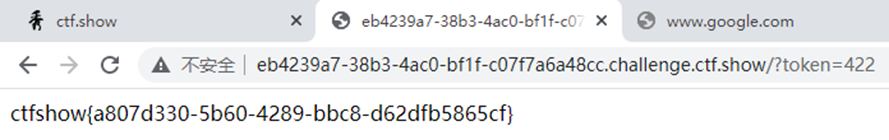
- flag
web24
- 源码:
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-03 13:26:39
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-03 13:53:31
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
include("flag.php");
if(isset($_GET['r'])){
$r = $_GET['r'];
mt_srand(372619038);
if(intval($r)===intval(mt_rand())){
echo $flag;
}
}else{
highlight_file(__FILE__);
echo system('cat /proc/version');
}
?> Linux version 5.4.0-126-generic (buildd@lcy02-amd64-072) (gcc version 9.4.0 (Ubuntu 9.4.0-1ubuntu1~20.04.1)) #142-Ubuntu SMP Fri Aug 26 12:12:57 UTC 2022 Linux version 5.4.0-126-generic (buildd@lcy02-amd64-072) (gcc version 9.4.0 (Ubuntu 9.4.0-1ubuntu1~20.04.1)) #142-Ubuntu SMP Fri Aug 26 12:12:57 UTC 2022
- hint

- 根据hint写php脚本
<?php
mt_srand(372619038);
echo (mt_rand());
?>
- flag

web25
- 源码:
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-03 13:56:57
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-03 15:47:33
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
include("flag.php");
if(isset($_GET['r'])){
$r = $_GET['r'];
mt_srand(hexdec(substr(md5($flag), 0,8)));
$rand = intval($r)-intval(mt_rand());
if((!$rand)){
if($_COOKIE['token']==(mt_rand()+mt_rand())){
echo $flag;
}
}else{
echo $rand;
}
}else{
highlight_file(__FILE__);
echo system('cat /proc/version');
}
Linux version 5.4.0-126-generic (buildd@lcy02-amd64-072) (gcc version 9.4.0 (Ubuntu 9.4.0-1ubuntu1~20.04.1)) #142-Ubuntu SMP Fri Aug 26 12:12:57 UTC 2022 Linux version 5.4.0-126-generic (buildd@lcy02-amd64-072) (gcc version 9.4.0 (Ubuntu 9.4.0-1ubuntu1~20.04.1)) #142-Ubuntu SMP Fri Aug 26 12:12:57 UTC 2022
- hint
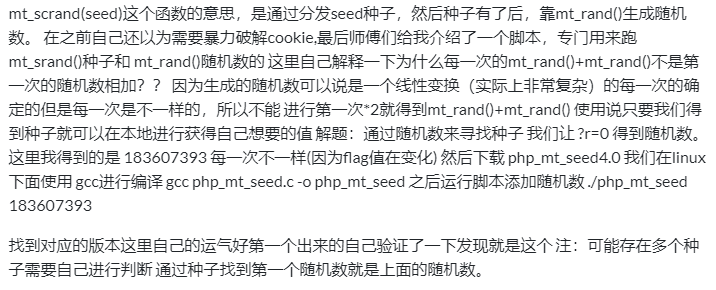
- 可以先通过r=0 得到mt_rand()第一个值为539472865
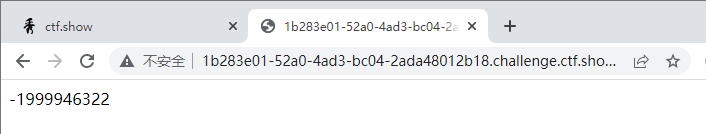
- 再利用php_mt_seed-4.0推出种子

- 通过这两行代码,去计算出token,其中seed的选择要与自己题目用到的php版本相近的seed
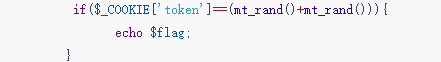
- 我的php版本是php7.3.11
- 计算token代码

- flag
web26
- 打开题目后一直下一步,不输入任何东西,直接burp抓包后直接repeater发包就能得到flag(这应该算是非预期吧)
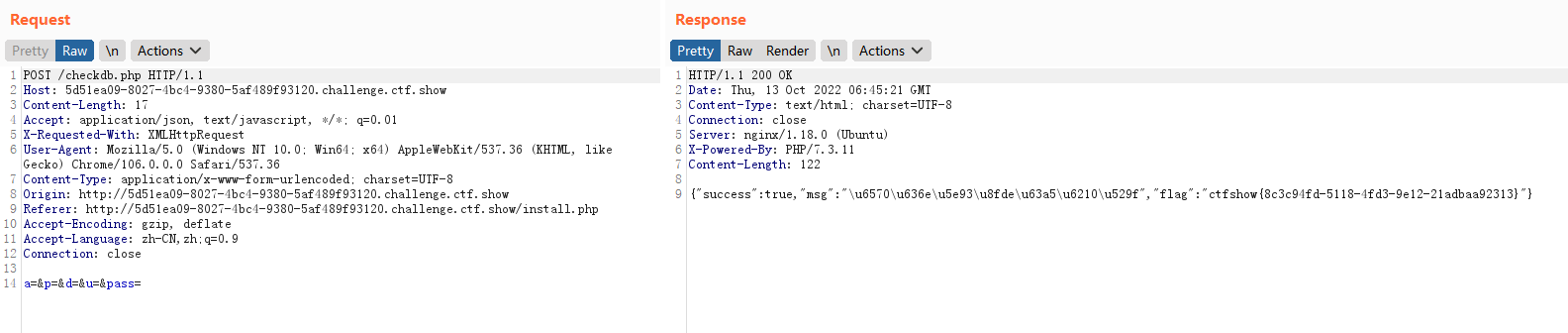
- 正常的做题姿势
- burp抓包后用Intruder模块进行爆破
web27
- 打开题目,得到一份录取名单,教务管理系统,学院录取查询系统
- 得到身份证信息不清晰,那就抓包爆破

- 成功爆破出完整的身份证号码
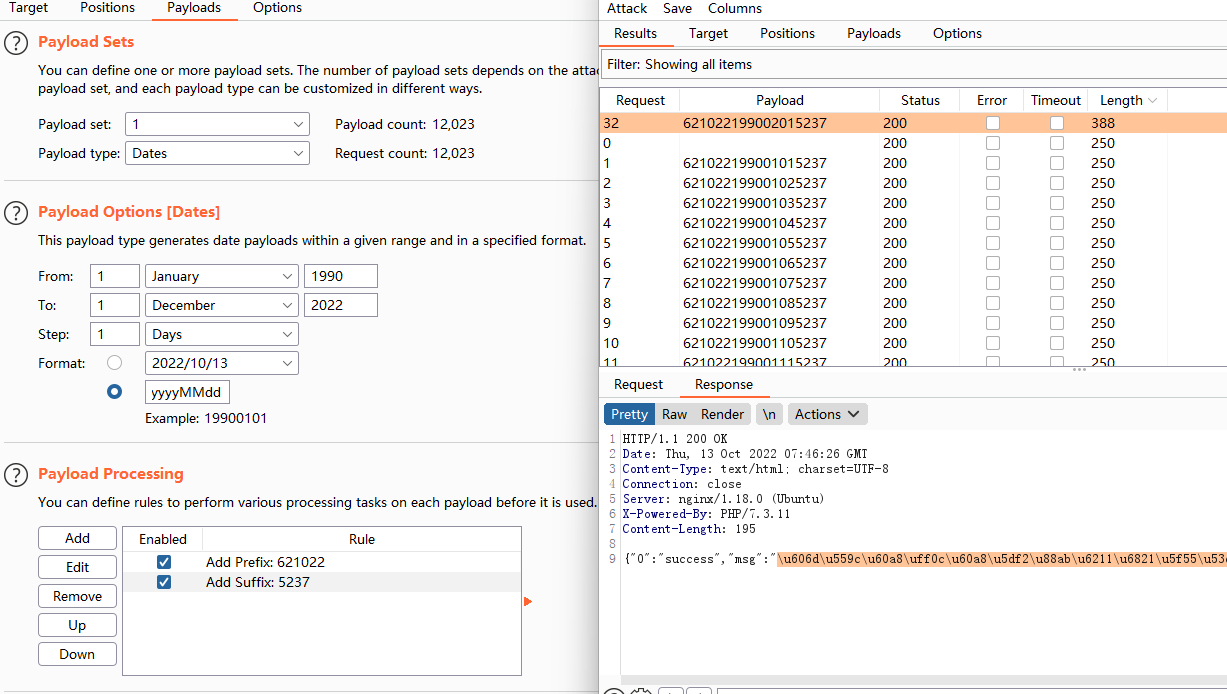
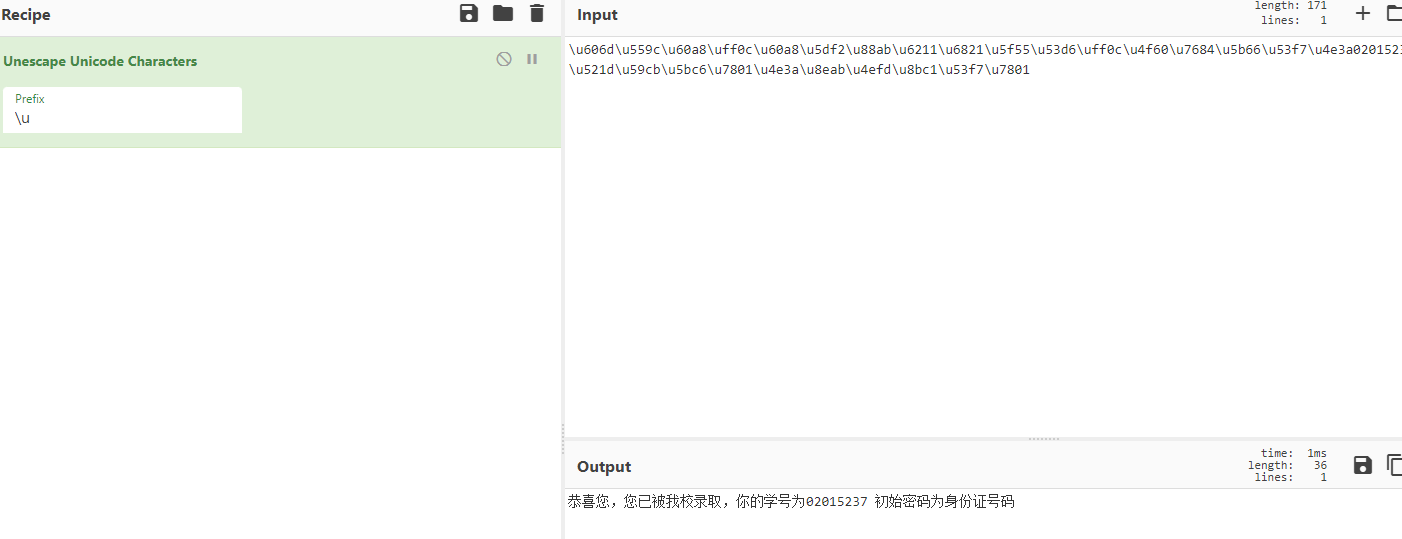
- 解出响应包的Unicode编码,得到学号和密码
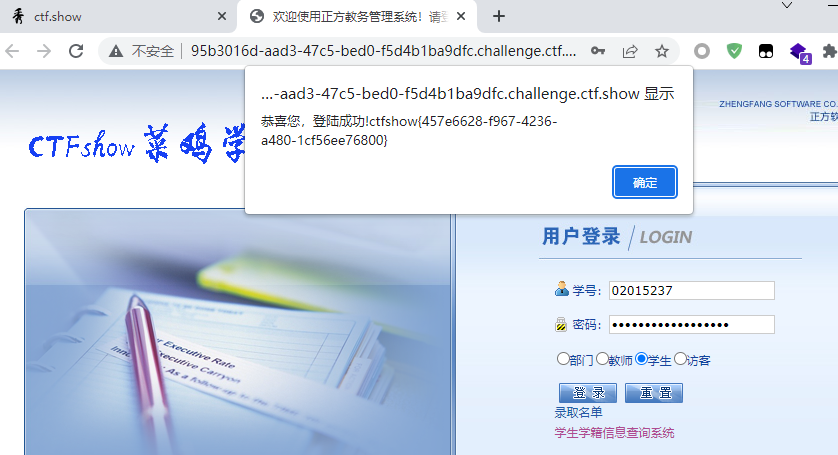
- flag
web28
- 题目
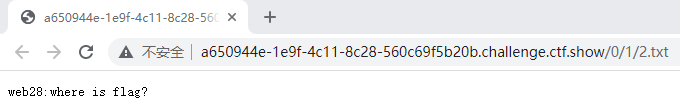
- hint
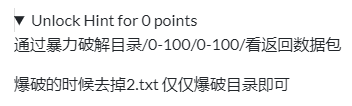
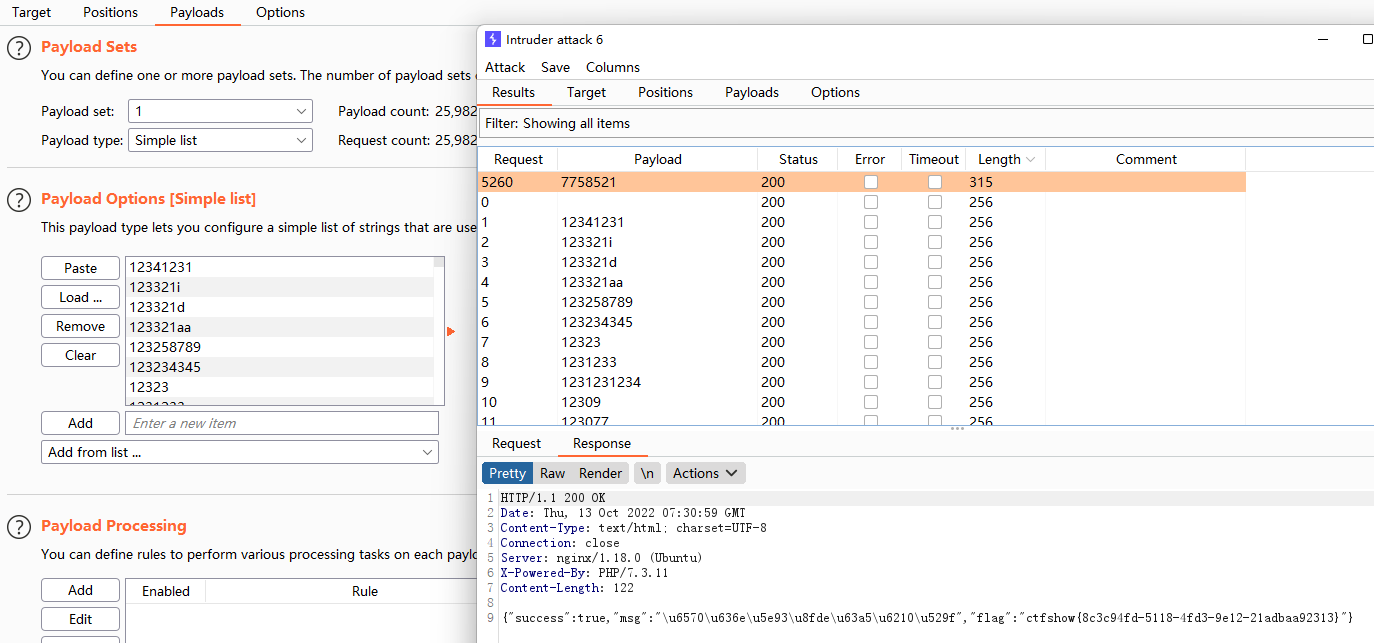
- 抓包爆破
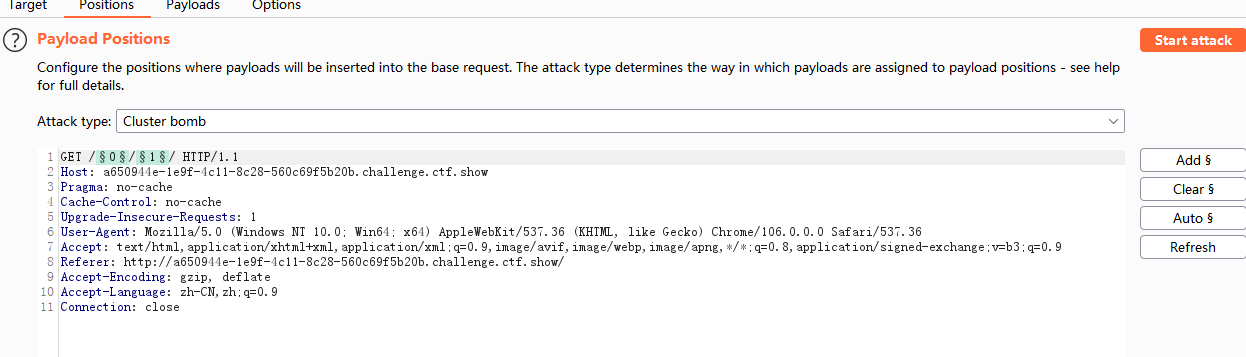
- payloads设置:1和2都是一样
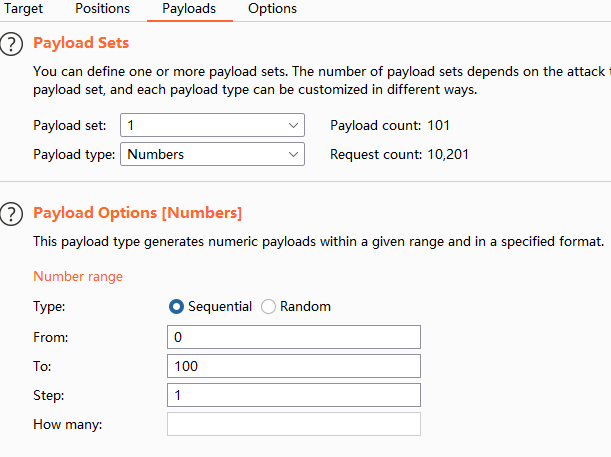
- 爆破成功
