2023年某比赛awdp(个人赛)
题目名称:hahaNode(防御)
操作内容:
把\src\routes\index.js里的第7行和第12行的两个admin都改成复杂点的密码 修改后的代码:(红色部分为修改部分)
var express = require('express');
var route = express.Router();
function isAdminValid(username){
return (
String(username).length >= 1 && String(username).toLowerCase() !== "admin27637621683_jdhfshkdjh".toLowerCase()
)
}
function isAdmin(username){
return String(username).toUpperCase() == "admin23y1_832482774nzxbmnczx".toUpperCase();
}
route.get('/', function(req, res, next) {
res.render('index')
});
route.post('/', function(req, res, next) {
var username = req.body.username
var profile = req.body.profile
if(isAdmin(username) && isAdminValid(username)){
res.render('index', profile)
}else{
var notadmin = new Object();
notadmin.name = String(username)
notadmin.bio = String(username)
notadmin.position = String(username)
res.render('index', notadmin);
}
});
module.exports = route;
题目名称:ezphp(防御)
操作内容:
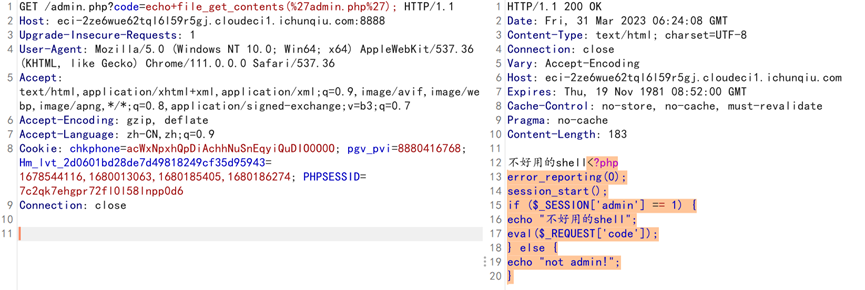
使用万能密码登录,然后进行抓包,并构造payload读取admin.php文件
然后注释eval($_REQUEST['code']);